Shut the Door, Before They Get In!
Stop social engineering attacks.

Social engineering is big business
Impersonation attempts are on the rise
And A.I. is making it harder to tell what is fake
The weapon of choice in most cases is impersonation, with this strategy accounting for 89% of total business email compromise (BEC) attempts, with the most-impersonated individuals being: 5
CEOs and Executives (57%)
Directors, Managers, and Supervisors (26%)
IT Personnel (9%)
40% of BEC emails uncovered in Q2 2024 were
AI-generated.6
Sources: Vipre5, Vipre6
The new hunting ground: Vishing

Voice, once the dominion of spammers and scam calls, has become rife with hackers through vishing attacks.
Vishing grew 440% in the latter half of 2024.7
Deepfake vishing grew by 1600% in Q1 2025.8
Sources: Crowdstrike7, Right-Hand Cybersecurity8
Why is vishing so popular?
Bypasses spam and phishing filters
Communicates emotion and urgency better
Builds better rapport and sympathy
Easier to convince the target to take action
Circumvents automated identity-verification tools
Generative AI makes creating realistic scripts easier.
Deepfake voice technology is significantly more sophisticated than a year ago

“What's more effective than a phishing email that looks like it came from your CEO?
A deepfake vishing phone call that sounds like him.”
Michael Courter, Black Door Solutions
The latest target: Technical Helpdesks
Hackers are targeting technology admins and helpdesk personnel at alarming rates.
66% of social engineering attacks targeted privileged accounts.9
Their favorite targets include:
IT helpdesks
Technology owners and admins
HR admins
Customer technical support
9 Unit42

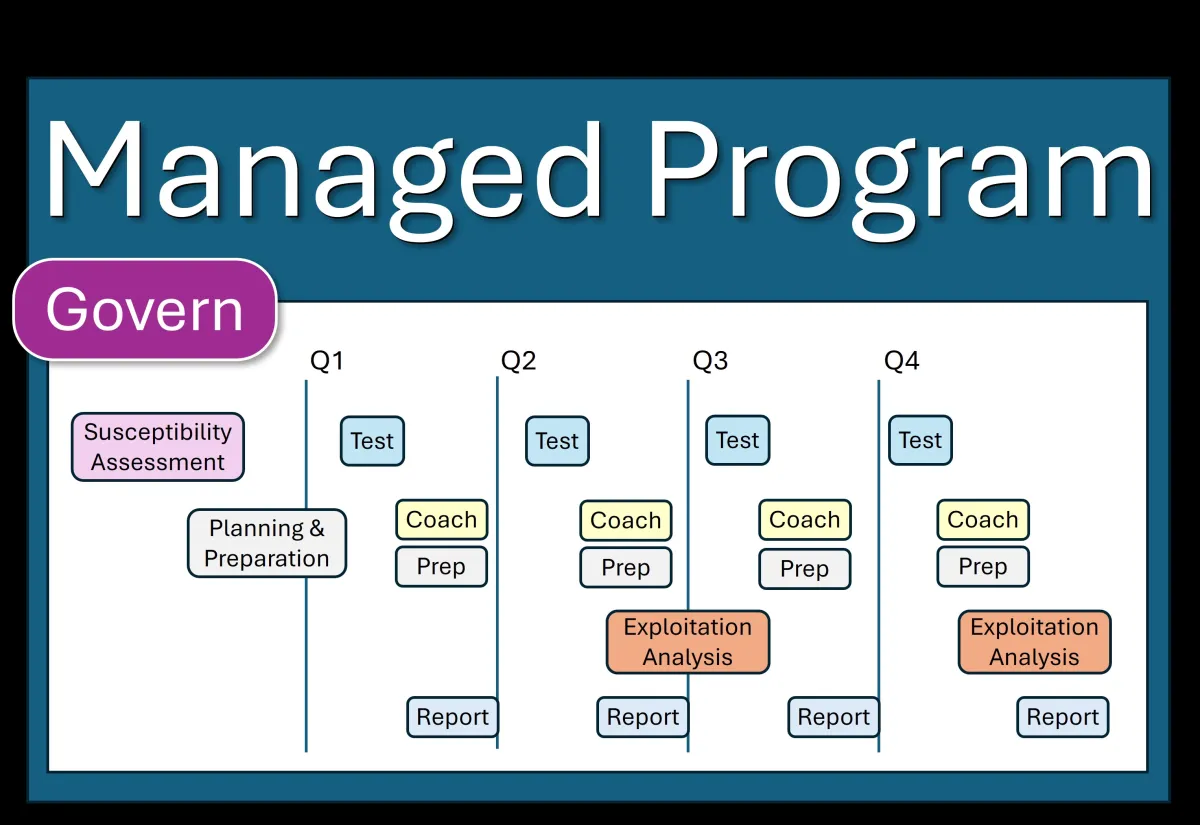
Typical Customer Journey
Unknown Susceptibility
Organizations often don't realize how susceptible they are to social engineering attacks or which staff are most at risk
Identify At-Risk Staff & Assets
Using a Susceptibility Profile as a guide, we help leaders identify their most at-risk staff and digital assets.
Perform Testing
We prepare campaigns, scenarios, and scripts specifically targeting at-risk staff. We execute tests per rules of engagement.
Define Action Plan
We work with leaders to develop an action plan, which typically includes coaching and refining training and testing materials
Services
How we help our clients

Red Team
Our ethical hackers provide realistic adversary emulation and penetration testing to identify gaps and vulnerabilities. They provide advisory and remediation support to help your blue team and system owners to work together to improve your organization's security posture.

Social Engineering
A specialty of our Red Team, we provide susceptibility profiling, social engineering penetration testing, coaching & education, exploitability analysis, and program management to enable your organization to proactively shut the door on social engineering attacks.

Program Maturity
A specialty of our Red Team, we provide susceptibility profiling, social engineering penetration testing, coaching & education, exploitability analysis, and program management to enable your organization to proactively shut the door on social engineering attacks.

Advisory
A specialty of our Red Team, we provide susceptibility profiling, social engineering penetration testing, coaching & education, exploitability analysis, and program management to enable your organization to proactively shut the door on social engineering attacks.

Secure R&D
A specialty of our Red Team, we provide susceptibility profiling, social engineering penetration testing, coaching & education, exploitability analysis, and program management to enable your organization to proactively shut the door on social engineering attacks.

AI & Next Gen
A specialty of our Red Team, we provide susceptibility profiling, social engineering penetration testing, coaching & education, exploitability analysis, and program management to enable your organization to proactively shut the door on social engineering attacks.
Want to work with us?
Have a question or want to make sure that our services are right for you?

COMPANY
SERVICES
LEGAL
FOLLOW US
Copyright 2026 Blackdoor Solutions. All Rights Reserved.